Some of you may have heard about VPN protocols that let you establish a connection between your device and a server, such as OpenVPN and IPsec. But there’s a brand new shiny protocol that promises to be faster and more secure at the same time — WireGuard.
But WTF is a VPN anyway? A VPN is a virtual private network between a device in front of you and a server in a data center. If you want to hide your internet traffic from other people on your local network, you can create a tunnel between your device and a server.
All your network traffic will go through this connection, and traffic is usually encrypted from one end to the other. It means that your overzealous IT department or the Great Firewall of China can’t block any service.
And yet, it also means that the person who operates the server can see all unencrypted traffic. That’s why I never recommend using a free VPN service or even paying for an account. Using a VPN doesn’t mean that you’ll be more secure on the internet. You’re just moving the risk down the VPN tunnel.
Many VPN companies analyze your browsing habits, sell them to advertisers, inject their own ads on non-secure pages, steal your identity, log your internet traffic, share information with law enforcement and more.
When it comes to VPN companies, trust no one.
Looking at the protocols
There are multiple ways to create a point-to-point VPN tunnel. Your device and the server need to use the same protocol to talk to one another. The most popular protocol is OpenVPN. It’s a secure implementation that works on pretty much any device, as long as you’re willing to install an app.
IPsec, combined with IKEv2 authentication, is another popular protocol. It works natively on iOS, macOS, Windows and Linux. That’s why it’s a great option for devices where you can’t install any app you want.
You may have also heard about PPTP or L2TP as well. But those protocols aren’t as secure and nobody should use them anymore.
It seems like there are plenty of options already. But OpenVPN has been around for 17 years. It is slow and it was never designed for mobile devices.
OpenVPN and IPsec also have a huge codebase, which creates a bigger attack surface. It’s unclear whether the NSA has found vulnerabilities in those protocols because it’s harder to audit big codebases. WireGuard creator Jason Donenfeld only wrote 4,000 lines of code for the initial release.
Connecting to a WireGuard server is pretty much like connecting to a remote server using SSH. You generate a set of public and private keys and exchange public keys with the server. It’s both secure and hard to fool.
Compared to other VPN protocols, WireGuard relies on your device’s network interfaces. It adds a new interface to natively route all traffic through the tunnel, whether you’re using Wi-Fi, Ethernet, LTE, etc.
Regular VPN users also know that you have to reconnect to the VPN server every time you switch from Wi-Fi to LTE to Ethernet… WireGuard servers can maintain the connection with your device, even if you switch to another network and get a new IP address.
WireGuard is still quite new and experimental. For instance, you won’t find any WireGuard client for iOS. There are also very few WireGuard implementations with a graphical user interface.
Building your own VPN server
If you want to give WireGuard a try, it’s not that hard. You may remember that I talked about Algo VPN in the past. It’s a great open source project that lets you set up your own VPN server in just a few minutes. You don’t need any coding skill.
It turns out Algo VPN now supports WireGuard in addition to IKEv2. In other words, creating a VPN server with Algo VPN will let you connect to this server using both protocols.
Algo VPN runs on any Ubuntu server, but the easiest way to host your server is to create an account on DigitalOcean. After that, you’ll need to download a zip file and follow the instructions.
Once the setup is done, you should have a new folder on your hard drive with everything you need to connect to your VPN server. If you’re on a Mac, you can double-click on the .mobileconfig file to connect to your VPN server from your Mac using IKEv2.
If you want to try WireGuard, you’ll need a computer that runs macOS or Linux, or an Android phone. The easiest way to use WireGuard is to install the Android app and add the .conf file to your phone.
On your Mac, you need to install WireGuard using Homebrew (brew install wireguard-tools). You can then move the myvpnserver.conf file to /etc/wireguard/ on your hard drive and connect using a simple command line (“wg-quick up myvpnserver” and “wg-quick down myvpnserver”).
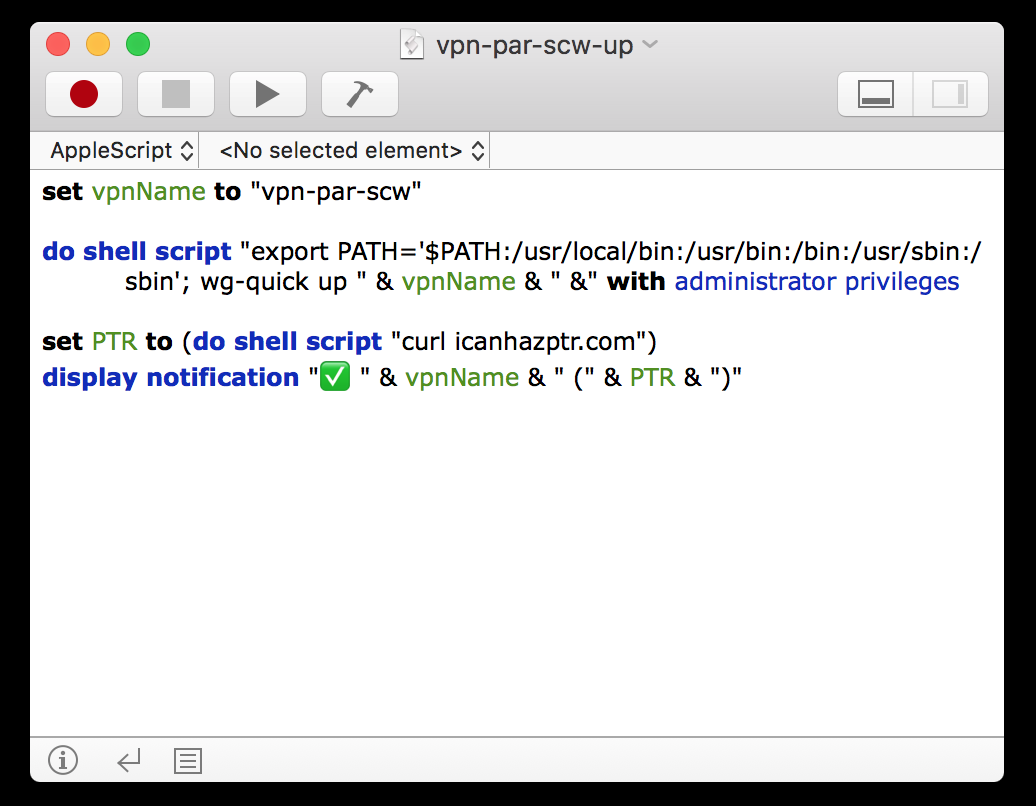
I wanted to go one step further and skip the Terminal window. On macOS, you can create an AppleScript using the Script Editor app and put it in your menu bar by enabling the menu bar option in the settings.
In my script, I also fetch my current hostname using icanhazptr.com. I then display my current hostname in a notification to check that I’m connected to the VPN server. In this case, I created a VPN server on Scaleway:
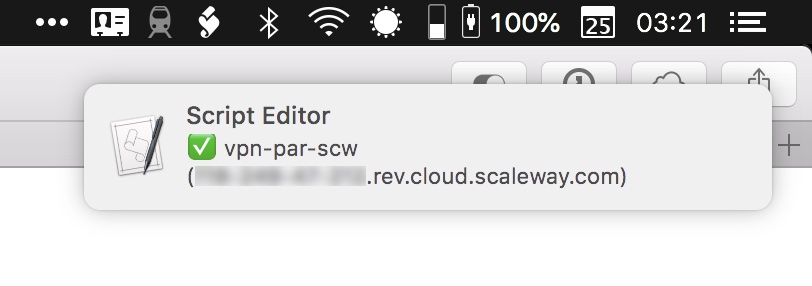
There you have it. Now you can’t say that you prefer to use a commercial VPN service because they have a nice menu bar app. This setup offers the same convenience but with a more stable VPN connection.
Once again, WireGuard is experimental. You need to assess your risks before using WireGuard at a production level. If you’re Edward Snowden, WireGuard might not be ready for you just yet. You also need to be comfortable with a buggy implementation. For instance, I had a DNS issue after shutting down a WireGuard connection, so I had to reset the DNS settings in my network interfaces.
But the fact that you can close your laptop, switch to another Wi-Fi network and stay connected to the VPN server is pretty neat. It’s clear that WireGuard represents the future of VPN protocols.
from TechCrunch https://ift.tt/2LIJXXn
No comments:
Post a Comment